
- Dito Legislative Insights - Production Deployment
- Setup Instructions
- 1. Remove Public IP Address from the VM
- 2. Set up a Cloud NAT Gateway
- 3. Create a Dedicated Service Account for the VM
- 4. Assign a Network Endpoint Group (NEG) to the VM
- 5. Create a Load Balancer to Expose the Application
- 6. Configure the OAuth consent screen
- 7. Create OAuth credentials
- 8. Setup IAP access
- 9. Verify Access Control
- 10. Configure API Keys
Dito Legislative Insights - Production Deployment
Setup and configuration of a secure production deployment environment is included with the Legislative Insights License. Our team will work with you to configure a secure environment following Google’s best practice guidelines as shown in the following diagram:
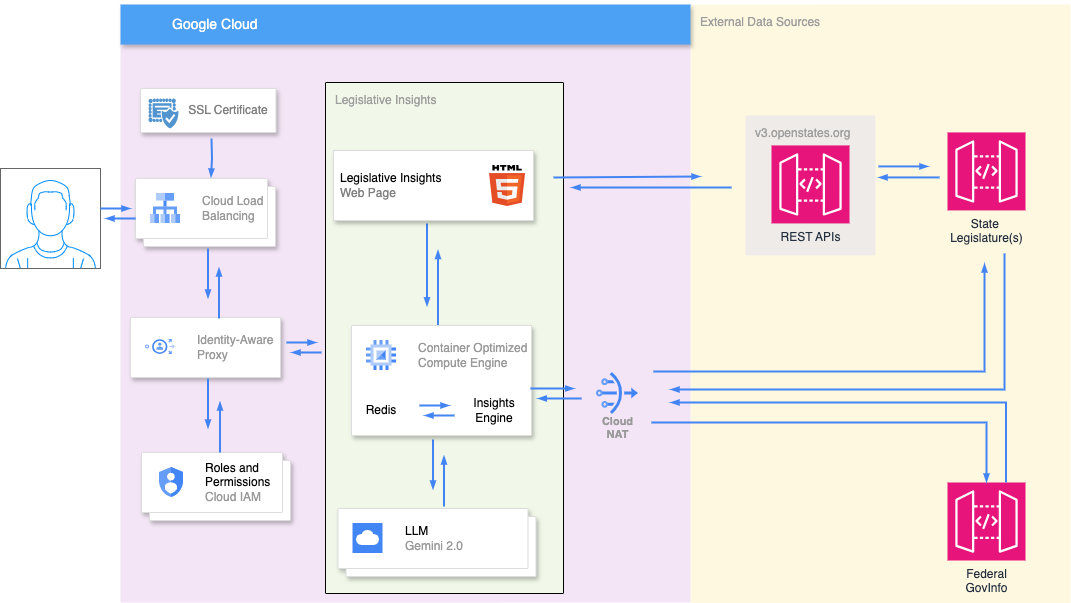
Users connect to the application via a load balancer that routes its requests through an Identity-Aware Proxy (IAP). IAP establishes a central authorization layer for applications accessed by HTTPS. Legislative Insights uses it to implement access control. Users are added to a Cloud IAM group which is granted permission to access the application. IAM verifies these permissions for each request to the application and grants or denys access as appropriate.
Authorized users are granted access to a single page application. It makes client side requests to the OpenStates API to identify URLs for State bills. URLs are submitted to the Insights Engine for processing. The Insights Engine proxies requests for these URLs to State Legislatures. It downloads PDF copies of legislative bills, extracts their text and facilitates analysis using an LLM. A similar process is followed for Federal legislation. A Cloud NAT Gateway is required for the Insights Engine to communicate with external resources.
Setup Instructions
This document outlines the steps involved in this to restrict access to the service using Identity-Aware Proxy (IAP). The process involves removing the public IP address from the VM, assigning a dedicated service account, creating a Network Endpoint Group (NEG), setting up a load balancer, and configuring IAP to control access.
Overview
- Remove Public IP Address from the VM
- Set up a Cloud NAT Gateway
- Create a Dedicated Service Account for the VM
- Assign a Network Endpoint Group (NEG) to the VM
- Create a Load Balancer to Expose the Application
- Configure the OAuth consent screen
- Create OAuth credentials
- Setup IAP access
- Verify Access Control
- Configure API Keys
Prerequisites:
Before you start, identify the fully qualified domain name (FQDN) that you want to associate with the application. You will need to create an A-Record associating it with the IP address of the load balancer that this process creates.
Procedure:
1. Remove Public IP Address from the VM
- Stop the VM
Before making changes, stop the VM to safely modify its network interface. - Remove the Public IP Address
Once the VM is stopped, remove the public IP address to ensure that the VM is only accessible internally. - Start the VM
Restart the VM after removing the public IP address. Use a browser to verify it is no longer available
2. Set up a Cloud NAT Gateway
Once the VM’s public IP address has been removed Legislative Insights will no longer be able to submit proxy requests to download bills. Configure a Cloud NAT Gateway to enable Network Address Translation (NAT) in the GCP Project to reenable this functionality
- Follow the Cloud NAT set up instructions for a Public NAT
3. Create a Dedicated Service Account for the VM
-
Create a Service Account
Create a dedicated service account to be used by the VM. - Assign IAM Roles assign the following IAM roles to the service account:
- Cloud Infrastructure Manager Agent
- Compute Admin
- Service Account User
- Attach the Service Account to the VM
Update the VM to use the new service account.
4. Assign a Network Endpoint Group (NEG) to the VM
- Create a Health Check
First, create a health check to ensure the VM is running and healthy. The health check should verify the http service is responding to TCP requests on Port 80. - Create a Network Endpoint Group (NEG)
Create or identify a Zonal Network endpoint group (NEG) for to use as a backend in a load balancer from the GCP Console - Attach the VM to the NEG
Use theADD NETWORK ENDPOINTbutton on the GCP Console’s NEG screen to add the VM to the NEG.
5. Create a Load Balancer to Expose the Application
Create a Global external Application load balancer:
- Use a Google Managed Certificate as a frontend with the FQDN identified earlier
- and a Zonal NEG as a backend.
- Make sure CDN is disabled for the backend service as IAP is not supported for CDN backed resources.
Wait for the load balancer to deploy and then test access using a browser. At this point Legislative Insights should be accessible to the public internet. The following steps will restrict this access to a named list of users.
6. Configure the OAuth consent screen
Follow the instructions in the Google documentation
- Open the GCP console and navigate to the OAuth consent screen under APIs & Services
- Select
Internalas User Type if all your users are Google Workspace organization orExternalto allow gmail and other Google identities then hit theCreatebutton. - Enter an App name and support email address then click
Save.
7. Create OAuth credentials
- Navigate to to the Credentials page under APIs & Services
- Select Web application in the Application type drop down, supply an name and click
Create.
This will open a dialog showing a newly created OAuth client ID and secret. - Copy the client ID to the clipboard and use the Download JSON link to save the credentials for later use.
- Add a universal redirect URL to the authorized redirect URIs field in the following format:
https://iap.googleapis.com/v1/oauth/clientIds/CLIENT_ID:handleRedirect
where CLIENT_ID is the OAuth client ID you copied to the clipboard.
8. Setup IAP access
- Optional create an IAM Group in your organization to identify users who will have access to the application.
- Navigate to the Identity-Aware Proxy page under Security. You should see an entry for the load balancer backend service. Select the checkbox at the start of the row and hit the
Add Principalbutton on the right of the screen. - In the Add principals dialog that appears, enter the email addresses of groups or individuals who should have access the application. Select IAP-secured Web App User in the Role field and hit
Save - Use the toggle control to enable IAP.
9. Verify Access Control
- Test Access
Attempt to access the application via the load balancer URL. Users with the appropriate IAM permissions should be able to authenticate via IAP and access the application. - Confirm Restricted Access
Verify that users without the iap.httpsResourceAccessor role are denied access. - Remove any Unnecessary Access
Review and remove any unnecessary access permissions from the IAM policy to ensure only the intended users have access to the application.
10. Configure API Keys
Once the environment has been secured and access restricted the authorized users, the environment can be configured to remove the requirement for individual users to provide a Google AI Studio API key in their browser before use.
Copyright © Dito LLC, 2022, 2025